Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Microsoft 365
NC Protect for Microsoft 365 and SharePoint Advanced Information Protection & Compliance
Organizations have sensitive data spread across on-premises and cloud based platforms. This present a major challenge for IT to ensure data integrity and security. NC Protect is both content and context aware to automatically find, classify and secure unstructured data on-premises, in the cloud and in hybrid environments.
Protecting and Managing Microsoft 365 Data
Microsoft 365 provides tools to assist with compliance, but they don’t provide native backup and recovery - they recommend customers backup their data with third-party applications. Rubrik’s SaaS-based approach to data protection for Microsoft 365 ensures critical data is secured, easily discoverable, and always accessible.
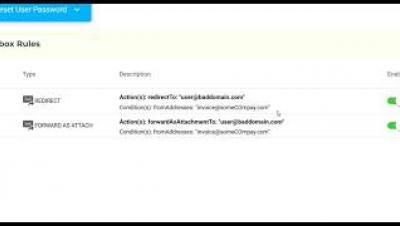
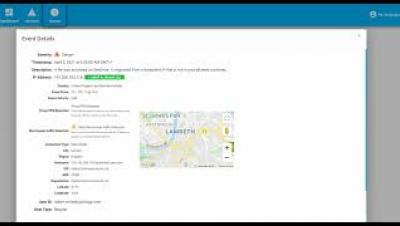
Stories from the SOC - Office 365 account compromise and credential abuse
Credential abuse and compromised user accounts are serious concerns for any organization. Credential abuse is often used to access other critical assets within an organization, subsidiaries, or another partner corporation. Once an account is compromised, it can be used for data exfiltration, or to further promote the agenda of a threat actor.
Remediate Office 365 Risks in App
Quickly Identify Mailbox or Configuration Risks in Office 365 and remediate them in a single click
Octiga Office 365 Security Quick Demo
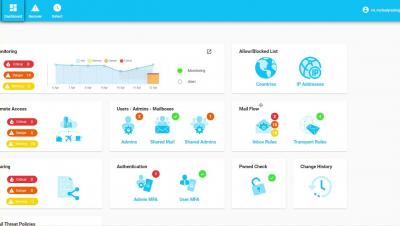
Prevent, Detect, Alert, Remediate. Both Posture and Breaches
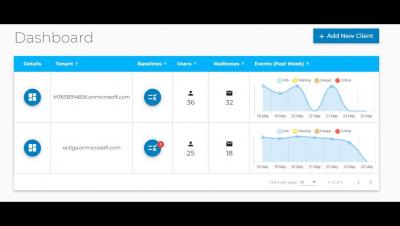
Octiga Monitored Baselines for Continuous Posture
Octiga All in one Office 365 Security Allows you to Setup, Monitor and remediate Security Posture while also detecting Breaches.
NIST Cybersecurity Framework for Office 365
With more than a decade long history of businesses adopting cloud computing, less than one-third of the enterprises have a documented cloud strategy as per Gartner's estimation. Despite the increased migration to cloud security, we discussed the top cloud security risks that security experts are afraid of today.