Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SecOps
Arctic Wolf Managed Security Awareness
Threat Intelligence, Integration and Automation in a Modern SOC
As organizations continue to evolve their security operations maturity and the SOC increasingly focuses on detection and response, three capabilities are foundational for success – threat intelligence, integration and automation. In a recent webinar, “Evolution of CTI – Use Case in a Modern SOC,” ThreatQuotient’s Yann Le Borgne, together with Ben van Ditmars of Atos and Martin Ohl from McAfee tackle this topic.
Elastic and Swimlane partner to deliver an extensible framework for the modern SOC
Today I’m happy to share more about our partnership with Swimlane, which further reinforces our commitment to empowering security teams everywhere. Today’s security teams rely on the power of Elastic’s high-speed, cloud-scale analytics to solve their most complex and pressing security issues. Swimlane’s security automation platform provides a way for these same teams to accelerate and optimize their workflows for max efficiency and to solve SOAR use cases.
Arctic Wolf Managed Detection and Response
Simplify Automation and Orchestration with a Data-driven Approach to SOAR and XDR
On the heels of announcing the closing of $22.5 million in new financing as a result of strong performance in 2020, I’m proud of our team’s latest innovation that we’re announcing today, ThreatQ TDR Orchestrator is a new data-driven approach to SOAR and XDR that accelerates threat detection and response across disparate systems for more efficient and effective security operations.
Adopting a cloud first strategy for modernizing security operations
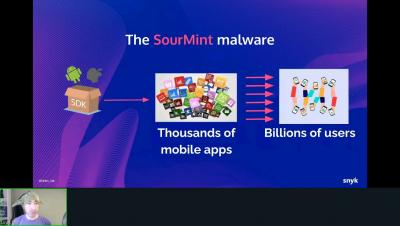
Are we forever doomed to software supply chain security?
What is a security operations center (SOC)? Explaining the SOC framework
If you’re responsible for stopping cyber threats within your organization, your job is more challenging than ever. The exposure to threats for any organization continues to escalate, and breaches are occurring every day. Consider: If your company doesn’t have a security operations center (SOC), it may be time to change that. In fact, a recent study indicates 86% of organizations rate the SOC as anywhere from important to essential to an organization's cybersecurity strategy.