Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Risk Management
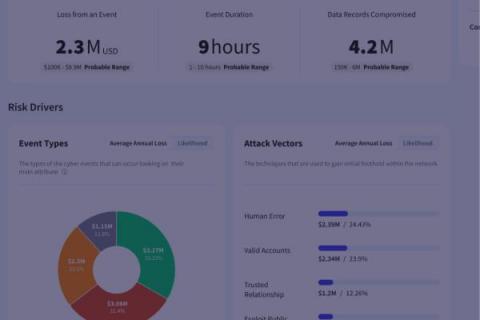
Cyber Security Risk Modeling: What Is It And How Does It Benefit Your Organization?
Continuous Monitoring for Real Time Compliance
Analysis of CVE-2023-2868 Exploitation: Campaign Targeting U.S. Entities Using Barracuda Email Security Gateway
CVE-2023-2868, a vulnerability in the Barracuda ESG was announced on May 23. On June 15th, a report surfaced, attributing the exploitation of this vulnerability to a threat actor group tracked as UNC4841, which analysts believe is conducting espionage on behalf of the Chinese government. SecurityScorecard’s STRIKE Team consulted its datasets to identify possibly affected organizations.
Continuous Security Monitoring - 5 Key Components
Prioritizing Actionable Insights: The Power of Effective Continuous Control Monitoring Combined with CRQ
How Vanta combines automation & customization to supercharge your GRC program
As the industry’s first automated compliance platform, Vanta includes a wealth of pre-built content, which enables customers without existing compliance processes to quickly get up and running. But more mature organizations may already have a compliance program — from the processes they follow to the definitions of their compliance and security surface area — that is built to meet their unique compliance goals, auditor requirements, and tech stack.
Underwriting Cyber Risk Part 2: Metrics to Track Cyber Hygiene
What is Cyber Threat Hunting?
Cyber threat hunting is a proactive security strategy that involves searching for threats within a network before they can cause significant damage. Unlike traditional methods, which are reactive and wait for an alert before taking action, threat hunting seeks to actively identify and mitigate hidden threats that have evaded initial security measures. Threat hunting involves constant monitoring and data analysis to spot suspicious behavior that may indicate a cyber attack.
What Your Auditor Looks for in Your Risk Management Process
TrustCloud teamed up with Dansa D’Arata Soucia on our Risk Rodeo webinar, to discuss everything you need to know to wrangle up risks with confidence. Our panelists weighed in on the four things that auditors look for in risk management processes.