ALPHV BlackCat Ransomware: A Technical Deep Dive and Mitigation Strategies
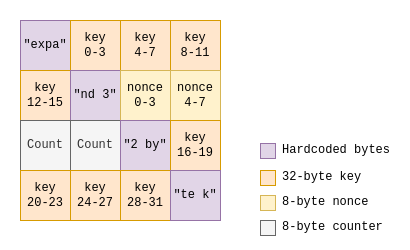
ALPHV, also known as BlackCat or Noberus, is a sophisticated ransomware group targeting critical infrastructure and various organizations, including being the most active group used to attack the financial services sector. ALPHV first appeared in November 2021 and operates on a Ransomware-as-a-Service (RaaS) model, allowing affiliates to use its malware for their own attacks in exchange for a cut of the ransom payments.