How Hive becomes one of the most dangerous ransomware group
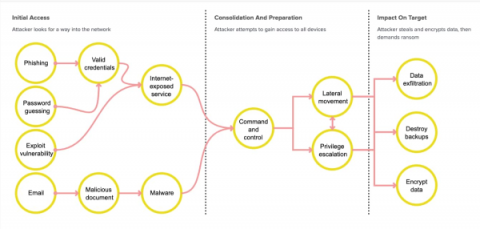
The Hive Gang is a Ransomware as a Service (RaaS) providers first identified in June 2021. Although relatively new, their aggressive tactics and ever evolving malware variants have made them one of the most successful RaaS groups of its kind. Find out how the group has risen through the ranks with their advanced ransomware kit, API based portal and negotiation services.