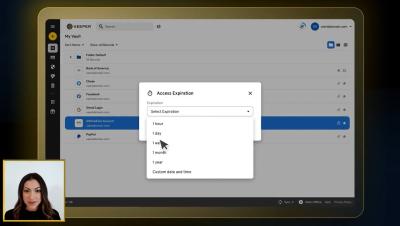
Introducing Time-Limited Access
As an enhancement to Keeper’s secure sharing capabilities, Time-Limited Access allows you to securely share credentials or secrets with other Keeper users on a temporary basis, automatically revoking access at a specified time. Time-Limited Access prevents long standing privileges and ensures that information is removed from the recipient’s vault, greatly reducing the risk of unauthorized access. Time-Limited Access brings several key benefits to users and administrators.