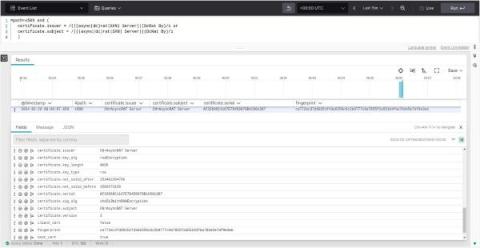
Hunt of the Month: Detecting AsyncRAT Malware Over HTTPS
Malware often hides communications with its command and control (C2) server over HTTPS. The encryption in HTTPS usually conceals the compromise long enough for the malware to accomplish its goal. This makes detecting malware that uses HTTPS challenging, but once in a while, you will catch a break, as in the case here with AsyncRAT, a Windows remote access tool that has been deployed over the past year to target organizations that manage critical infrastructure in the United States.