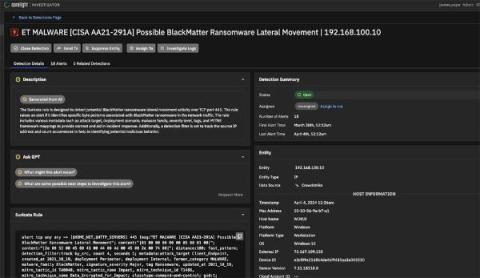
Streamlining Incident Response: How CrowdStrike Falcon EDR integration enhances threat detection
In the ever-evolving landscape of cybersecurity threats, staying ahead requires more than just detection; it demands comprehensive correlation and analysis for informed decision-making. Understanding the context surrounding an alert is important to effectively mitigate risk. That's why we're thrilled to announce the integration of CrowdStrike Falcon EDR with Investigator, part of Corelight’s Open NDR Platform.