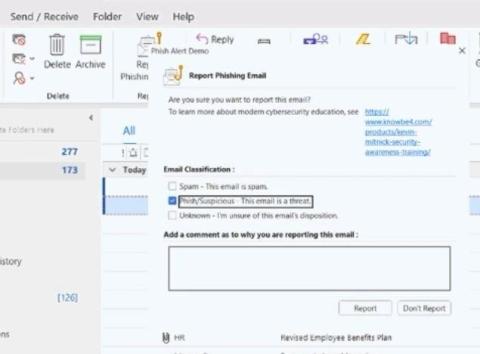
How To Defend Against the Rise of BEC Attacks
In 2023, the FBI’s Internet Crime Complaint Center (IC3) received 21,489 BEC complaints with adjusted losses over $2.9 billion USD, according to their 2023 Internet Crime Report. By way of comparison, ransomware, the cyber attack that grabs all the headlines and keeps IT and security teams up at night, accounted for only 2,825 complaints, with adjusted losses of less than $60 million USD.