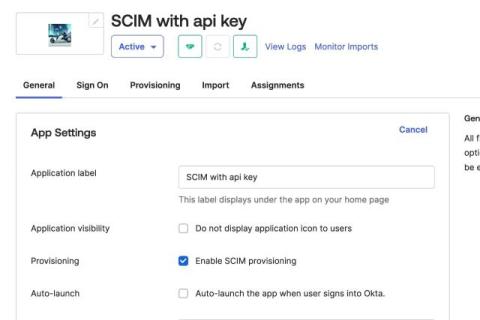
Rubrik powers Okta with critical user context to safeguard against identity attacks
Identity-based cyber attacks continue to prevail and impact organizations. Stealing credentials was the top initial action in breaches, according to Verizon. Plus, 84% of identity stakeholders surveyed said identity-related incidents directly impacted their business, resulting in reputational damages, distraction from core business, and increased recovery costs.