Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Elastic Security 8.7 helps security practitioners eliminate alert fatigue, drive MTTR lower, and better secure cloud environments
The Ultimate Guide to Sigma Rules
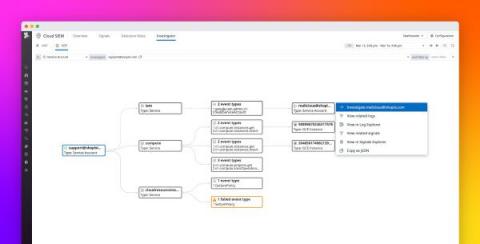
Visualize activity in your Google Cloud environment with Datadog Cloud SIEM Investigator
Cloud environments, in all their dynamic complexity, demand careful monitoring by DevOps and security teams. But the sheer abundance of telemetry data associated with the thousands of resources, users, and roles that comprise these environments can make monitoring a formidable task, causing security risks and other issues to be all too easily overlooked.
CLM and Turkish KVKK Personal Data Protection Law
CISO Leadership Panel: Tips on Hiring and Keeping SOC Talent
Due to economic pressures, staffing reductions, and lack of available talent, CISOs today are facing extreme pressure to do more with less. And retaining your best employees during tough times is becoming a major challenge across industries. Research at Devo shows SOC analysts are feeling stressed over too much work and not enough resources. In fact, more than 71% of SOC professionals we surveyed said they’re likely to quit their job because of information overload and lack of tools.
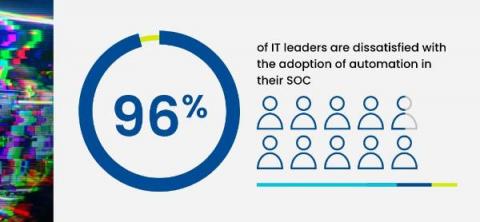
Key Security AI Adoption Trends for 2023
It’s hard to go a day without some headline touting how generative AI is transforming the future of work. And this sentiment certainly rings true in the security industry as security operations centers (SOCs) continue to mature their security posture with automation so that they can protect their enterprise and customer data. But how are leaders and teams feeling about the progress of AI adoption and how the tools are being used?
LimaCharlie vs a traditional SIEM
LimaCharlie offers many of the capabilities of a security information and event management (SIEM) solution, although it is not a SIEM. In this article, we’ll talk about LimaCharlie vs traditional SIEMs—and explain how our platform can be used to reduce or replace SIEM usage and help cybersecurity teams save money.