How Colleges & Universities Can Prevent Data Leaks
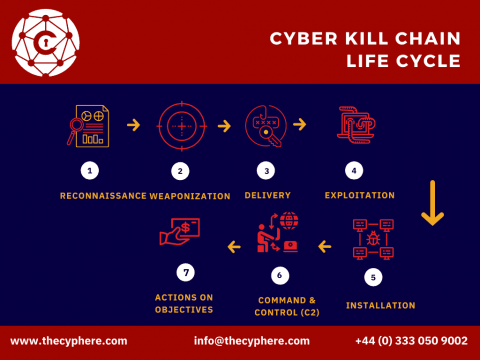
Data leaks occur when organizations fail to implement proper cybersecurity measures, causing sensitive data and other personally identifiable information (PII) to be exposed to the public. In most cases, data leaks occur due to internal human errors, an oversight by the IT committee, or a lack of strong security practices.