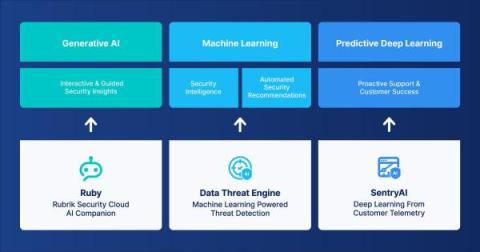
Unlocking the Power of Enterprise Data Security
By the year 2025, an estimated 463 exabytes will be created daily. For reference, one exabyte is 8,000,000,000,000,000,000 bits. That’s a lot of data. And even though cyber-attacks will increase as the attack surface expands, with cybercrime costing the world $10.5 trillion annually by 2025, data will remain the most valuable resource for today’s global enterprise.