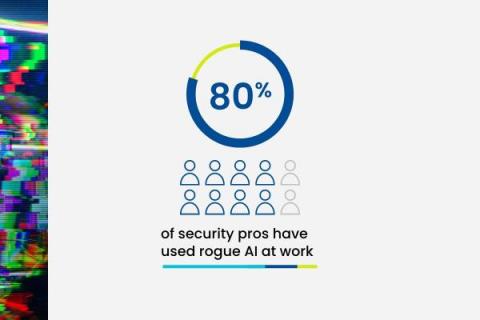
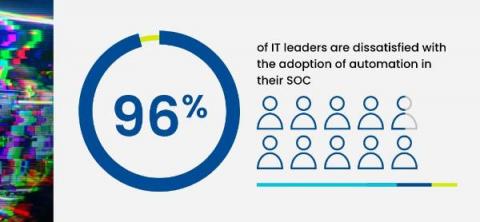
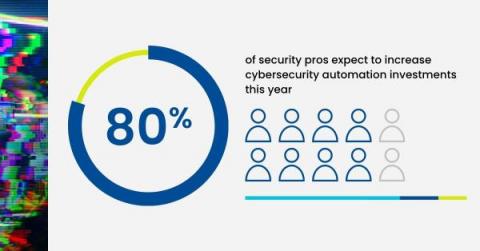
Rogue AI is Your New Insider Threat
When ChatGPT debuted in November 2022, it ushered in new points of view and sentiments around AI adoption. Workers from nearly every industry started to reimagine how they could accomplish daily tasks and execute their work — and the cybersecurity industry was no exception. Like shadow IT, new rogue AI tools — meaning AI tools that employees are adopting unbeknownst to the organization they work for — can pose security risks to your organization.