Understanding PCI DSS 4.0: What You Need to Know
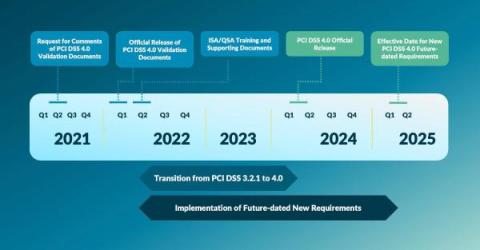
If you're in a business that handles credit cards, you already know how crucial it is to keep that data secure. PCI DSS is a set of compliance requirements that ensure all companies handling cardholder data keep it secure. And that it's not just a good idea—it's a must. As cyber threats become more sophisticated, it's challenging to keep pace with complex security and compliance landscapes.