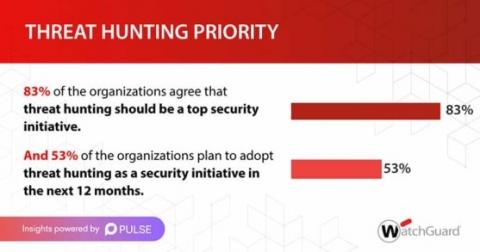
How are IT leaders approaching threat hunting?
Implementing robust defense strategies helps to mitigate the risk of cyberthreats in the early stages of an attack. Threat hunting, as part of this strategy, enables organizations to find those unknown threats that manage to bypass technology-based controls by detecting abnormal behaviors. With a number of challenges associated with executing a defense approach, how are IT leaders approaching this problem? Pulse and WatchGuard surveyed 100 IT leaders to find out.