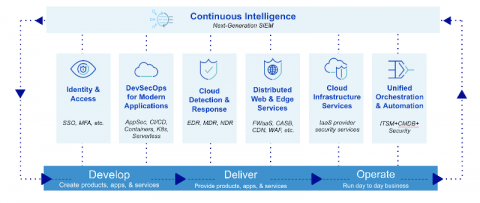
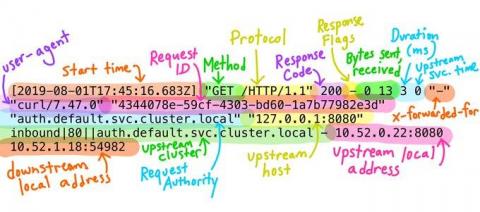
Automate your SIEM with Sumo Logic in 7 Clicks
At Sumo Logic Illuminate 2020, The Energy Authority’s IT Director for Service Delivery and Support Scott Follick spoke about the TEA, how they do things, what they have learned in the process of searching for a SIEM solution, and why they chose Sumo.