Sumo Logic and ZeroFOX Join Forces to Improve Visibility and Protect your Public Attack Surface
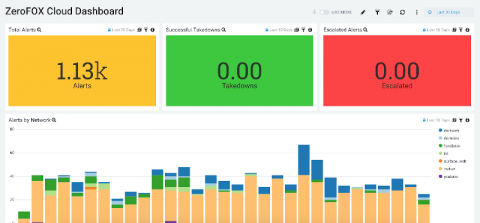
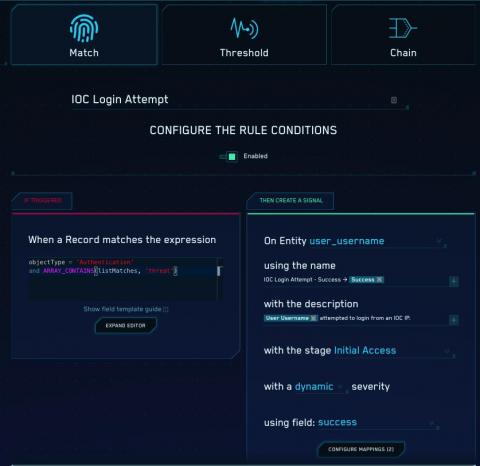
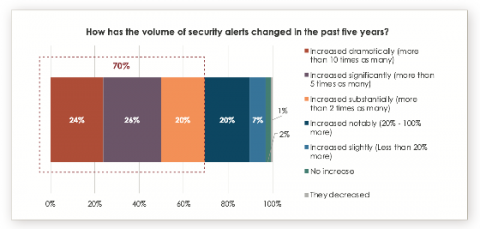
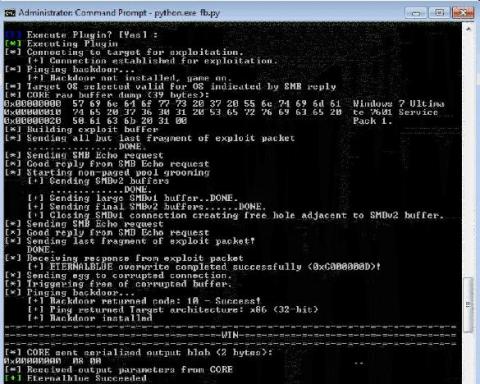
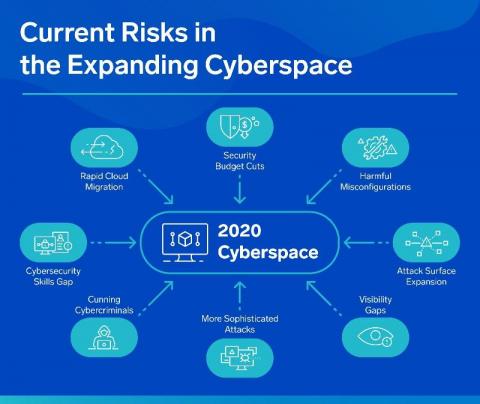
Today’s organizations have the challenge of managing several different applications and software within their technology stack. The more public-facing platforms an organization utilizes, the greater their public attack surface risks. Without proper protection, they and their community can become an easy target for malicious actors.