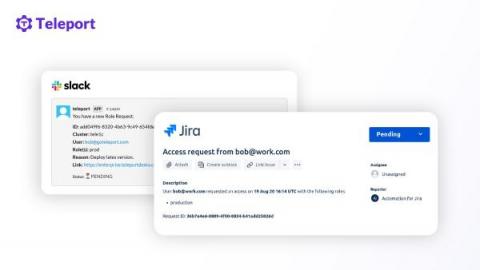
What is Zero Standing Privilege (ZSP)?
Zero standing privilege (ZSP) is an applied zero trust security strategy for privileged access management (PAM). The term zero standing privilege was coined by an analyst at Gartner. In practice, it implies no users should be pre-assigned with administrative account privileges. Zero-trust security forbids authorization based on static predefined trust boundaries.