SCARLETEEL 2.0: Fargate, Kubernetes, and Crypto
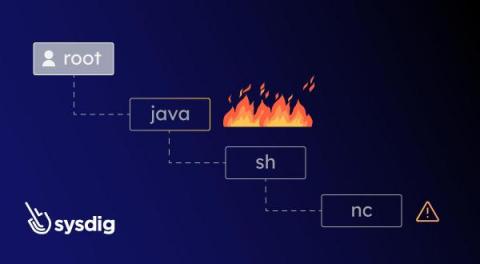
SCARLETEEL, an operation reported on by the Sysdig Threat Research Team last February, continues to thrive, improve tactics, and steal proprietary data. Cloud environments are still their primary target, but the tools and techniques used have adapted to bypass new security measures, along with a more resilient and stealthy command and control architecture.