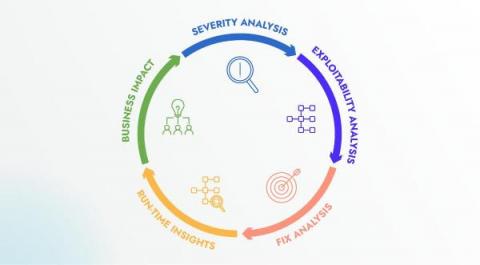
Boost Detection and Response with Cybereason and Sysdig
The Gartner 2021 Hype Cycle for Cloud reports 99% of breaches start with cloud misconfigurations. Thus, having a philosophy of protecting just traditional endpoints – servers, laptops, desktop PCs, and mobile devices – with EDR (Endpoint Detection and Response) software is not enough. Sysdig has teamed up with multiple security organizations in the cloud security ecosystem to offer comprehensive security solutions.