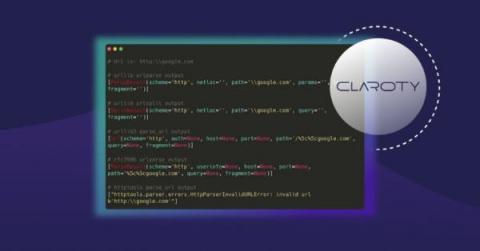
PHP security in Snyk Code now GA
We recently announced our beta release for PHP support in Snyk Code, which brought with it the ability to identify potential PHP security vulnerabilities at the code level. After a successful public beta program, PHP security support in Snyk Code is now GA. 🎉🎉🎉 PHP is a popular programming language that is used by developers all over the world. In this blog post, we will take a look at some of the features of Snyk Code and how it can be used with PHP.