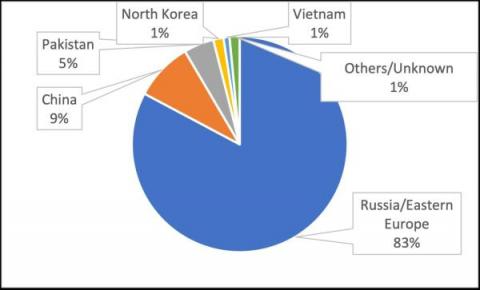
Hacking 101: What is pretexting?
Ever heard of pretexting? And no, we’re not talking about when you first carefully draft a risky text message before sending it! Pretexting is a sneaky and highly effective form of social engineering that attackers use to dupe people into sharing their personal information.