Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Teleport Cloud Enablement Series 101 - Joining Resources and Access Deep Dive
Teleport Cloud Enablement Series - User Migration, Logging, Troubleshooting, and Upcoming Features
How to Back up and Restore AWS Elastic Load Balancers for EKS Clusters
Load balancers are an integral component of any production environment. They allow the distribution of traffic across multiple available backend servers so that no single server becomes overwhelmed due to traffic. A load balancer can be configured for workloads running on AWS through the Elastic Load Balancer (ELB) service. At a high level, an ELB consists of 3 main components: AWS offers 3 different types of Elastic Load Balancers.
There's a New Stealer Variant in Town, and It's Using Electron to Stay Fully Undetected
Our threat research team recently uncovered new npm packages that are used to download a new info-stealer variant that uses the popular Electron framework to disguise itself as a legitimate application. In this blog post, we’ll analyze the attack flow of this new info-stealer we detected and explain how it can stay undetected by abusing trusted development tools like Electron.
Your Kubernetes cluster is not secure. Secure it with Kubescape!
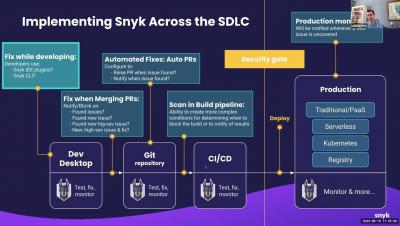
Starting Strategies: Where to Begin After Purchasing Snyk
Teleport Cloud Enablement Series 101 - Advanced Integrations and Security Features
Securing your CI/CD: an OIDC Tutorial
The article highlights the significance of securing CI/CD systems and offers three best practices. It introduces OpenID Connect (OIDC) as a means to employ short-lived tokens for improved security.
A New Version of Mend for Containers is Here
As modern software becomes increasingly cloud-based and containerized, application security tools must adapt to meet new challenges and provide security coverage across the software development lifecycle (SDLC). The use of container platforms like Docker and orchestration tools like Kubernetes inherently solves some security concerns – but containers are not without risk, and can even inject some new risks into your organization’s software.