Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
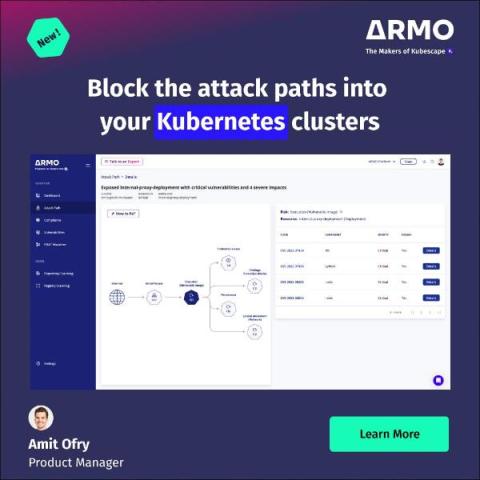
Block the attack paths into your Kubernetes clusters
Understanding PCI DSS v4.0
Add to Your AppSec Arsenal with Mend.io's Integration with Secure Code Warrior
We’re delighted to announce that Mend.io has launched a new integration with Secure Code Warrior®, a platform that provides secure coding training and tools that help shift developer focus from vulnerability reaction to prevention.
Let's Embrace Death in the Software Development Lifecycle
The leaves are turning brilliant colors before they fall off and blow away here where I live just a few minutes outside of Salem, Massachusetts where autumn — Halloween specifically — is a very big deal. I’m not morbid but it’s a natural time to think about how things wind down and finally breathe their last breath. Nothing lasts forever. Not trees. Not animals. Not people. Not cars. Not houses. Not software. Especially not software.
Navigating the Web: A Tale of Crafting Browser Extensions
Integrations101
GitGuardian Unveils "HasMySecretLeaked," Bringing Leak Detection to Every Secret In The DevOps Pipeline
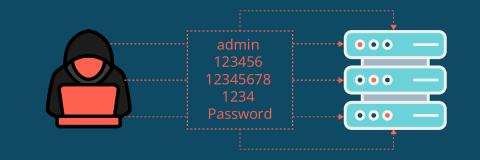
IT admins are just as culpable for weak password use
New data from Outpost24 reveals that IT administrators could be just as predictable as end-users when it comes to passwords. An analysis of just over 1.8 million passwords ranks ‘admin’ as the most popular password with over 40,000 entries, with additional findings pointing to a continued acceptance of default passwords.