Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Kubernetes Quick Hits: Don't run with privileged:true in you Kubernetes SecurityContext
Cloud Computing Security: A Primer
Gartner forecasts that worldwide public cloud end-user spending will grow 23% to USD 332.3 billion in 2021 as cloud technologies become mainstream. As cloud computing architectures continue to become more prevalent, “cloud native” has become a popular buzzword. But what exactly does “cloud native” mean and what impact does it have on security? How exactly do you secure all these cloud native applications?
Tagging Teleport Resources with Labels
Teleport has been named a Cool Vendor in Gartner's Identity-First Security report
Today we are happy to announce that Teleport has been included as a Cool Vendor in Gartner Cool Vendors in Identity-First Security report. “We believe Teleport’s inclusion in the Identity-First Security Report by Gartner is confirmation that Teleport solves a huge problem of accessing cloud-native resources that traditional PAM tools did not,” said Ev Kontsevoy, co-founder and CEO of Teleport.
Security at speed: Justifying your security program transformation using key development motivators
Security investments require executive buy-in. Learn what key development motivators can help justify your security program updates. As development speeds increase exponentially, organizations often struggle to introduce or maintain security practices capable of keeping pace. Additionally, security teams can find it difficult to get the top-down buy-in and support they need for a security overhaul.
The Biggest DevSecOps Hits From swampUP 2021
In the wake of recent events like the SolarWinds hack and the White House executive order on cybersecurity, DevSecOps and security are top-of-mind for most DevOps and security professionals. How to efficiently adapt or adopt a sound DevSecOps practice has become a priority, especially with the U.S. government’s impending mandate requiring software applications to be vetted, and to create a trusted Software Bill Of Materials (SBOM) for each one.
Getting started with Snyk for secure Java development
If you’re a Java developer that wants to develop your applications more securely, you’ve come to the right place. Snyk can help you with that mission. This article will explain how to begin with Snyk for secure Java development so you can be more secure from the get-go. If you’re new to Snyk, it’s important to know that we offer a variety of developer-focused products and tools. Some of these tools, like our CLI and some IDE integration, support multiple products.
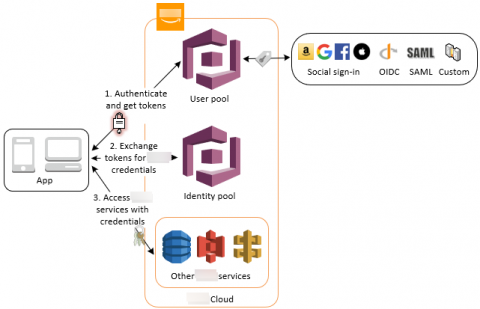
How does AWS IAM role, STS and Identity Pool work with each other.
We talked about IAM in the past 3 posts, identities in IAM, manage users privilege as an IT person and control privilege boundaries. We also talked about how applications use AWS Cognito Identity Pool to get AWS temporary credentials to access AWS resources in early posts of “What I wish I could have learned before starting using AWS Cognito” and “Authentication and authorization with AWS Amplify under the hood”.
Drive DevSecOps Visibility with JFrog Partner Integrations
If you need your teams to act, you need to alert them where they’re already looking. Yet yesterday’s DevOps practices demand individuals to wrangle with uncorrelated events, multiple UIs, and siloed technologies. Tomorrow’s DevOps must enable teams with: To practice DevSecOps, you’ll need to know where a vulnerable build has been deployed into production, and where to find the corrected build that should replace it.