Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
SSH Hardening Tips to Prevent Brute-Force Attacks
SSH servers are a common target for brute-force attacks. This is even more true if your infrastructure sits behind an SSH bastion because attackers have no choice but to compromise the bastion host either by exploitation or denial of service. In this article, we will list a few controls which will help you harden your SSH servers from brute- force attacks.
Chatting with the Log4JShell Bytecode Detector Creators
Styra 2021 Year in Review
It’s been a whirlwind year for Styra — from going fully remote as a company to raising $40 million in Series B Funding to more than doubling our workforce. We have a lot to be thankful for as a company, and before we say “goodbye” to 2021 and “hello'' to 2022, I wanted to take a moment to recap some of my favorite moments and initiatives of this past year.
SSH Bastion Host Best Practices
SSH bastion hosts are an indispensable security enforcement stack for secure infrastructure access. Every security compliance standard that deals with remote infrastructure access (e.g., FedRAMP AC-17 - Remote Access, HIPAA §164.312(a)(1) - Access control, SOC2 CC6.1 - Manage Points of Access) mandates preventing direct network access to the servers and APIs.
Welcoming Samantha Wessels: Snyk's New Vice President, EMEA Sales
What You Should Know About npm Packages 'colors' and 'faker'
Why Financial Services Companies That Value Agility & Security Pick Teleport
2022 feels a little different, doesn’t it? Every day I’m prepared to hear something new, something scary, or something exciting. These last couple of years have made it seem like we just never know what is coming next. It’s no different for financial services companies who have to be prepared for the unexpected, including disruptive technologies that can challenge their core businesses.
What You Need to Know About Adding a SaaS Component to Your Hardware or Software Business
Many market-leading companies who have dominated their respective sectors with hardware or on-prem/installable software solutions are turning to SaaS offerings to fuel the next phase of their growth. Why? Simple. Market valuations are much higher for SaaS companies than they are for traditional software and hardware companies. The median multiple on earnings for a SaaS company is 12.7x as of Q3 2021 according to venture capitalist Jamin Ball who tracks the Public Cloud Software (e.g.
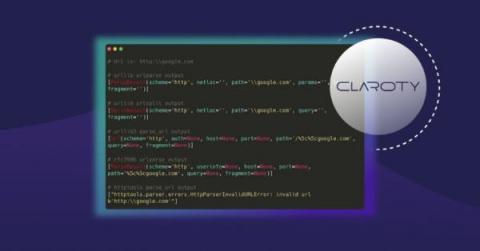
URL confusion vulnerabilities in the wild: Exploring parser inconsistencies
URLs have forever changed the way we interact with computers. Conceptualized in 1992 and defined in 1994, the Uniform Resource Locator (URL) continues to be a critical component of the internet, allowing people to navigate the web via descriptive, human-understandable addresses. But with the need for human readability came the need for breaking them into machine-usable components; this is handled with URL parsers.