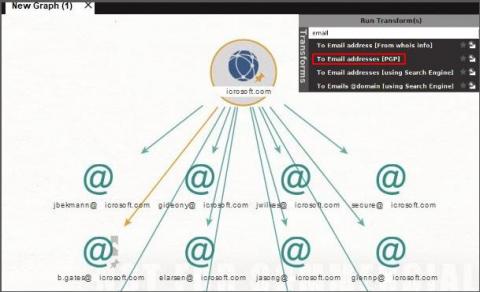
SMEs and the cyber security challenge
EasyJet, CapitalOne, British Airways and Marriott are all huge companies with equally large budgets. Another thing they have in common is they all fell victim to a serious data breach, costing them hundreds of millions of pounds. If the major players with a lot of resources to devote to cyber security still get hacked, do SMEs with limited budgets stand a chance? It’s a dramatic question, so let’s explore the answer.