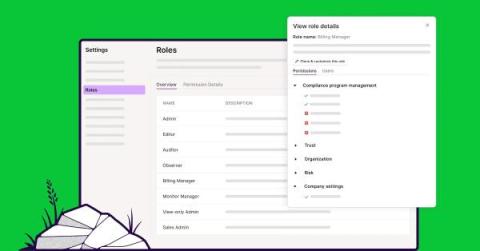
Introducing expanded Role-Based Access Control
Today we’re thrilled to announce that Vanta’s Role-Based Access Control (RBAC) functionality has gotten even stronger with new capabilities, including: These expanded RBAC capabilities are now generally available and demonstrate Vanta’s continued commitment to supporting the needs of larger, more advanced organizations through additional customization and flexibility across our platform.