Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Compliance
Things You Should Know About Your Privacy Online
Surveillance is becoming an increasingly standard component of modern life, posing a threat to the idea that people have a right to privacy. In many situations, we unwittingly provide companies with information about our preferences, routines, and interests. In this age of digital era, you must not rely on evolving surveillance regulations and vendors to keep your personal information and security intact.
Monitoring Transaction Log Files for PCI compliance
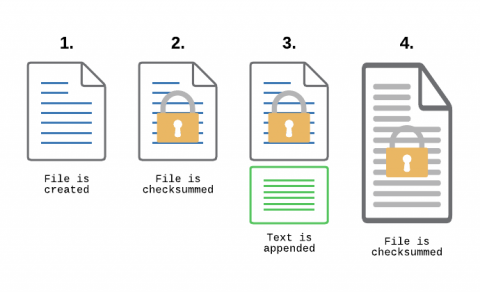
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
CrowdStrike Enables Federal Departments and Agencies to Meet CISA Operational Directive 23-01
In support of the Executive Order on Improving the Nation’s Cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA) recently published a Binding Operational Directive (BOD) 23-01, designed to improve cybersecurity for the Federal Civilian Executive Branch (FCEB) enterprise and their respective unclassified assets.
How Can POA&Ms Help Improve Your Security Budgeting Process?
Have you ever heard an IT security pro talk about their POA&M and wondered what they meant? You’re not alone. Many security consultants and engineers are uncertain about the meaning of the acronym “POA&M”. It stands for Plan of Actions and Milestones. It’s a commonplace term within military and defense working environments.
4 tips to achieve Data Compliance
Data compliance is a crucial and essential factor in organizations that should be carefully followed for data management. Data compliance is more than maintaining relevant standards and regulations and ensuring that the data is secured. The substantial amount of data that is processed and used in organizations must be managed properly. All phases of data access, usage, modification, and storage should be governed by correct policies, protocols, and standards.
Riscosity State of the digital supply chain Mike Hamilton and Barak Engel
The dark side of AI energy consumption - and what to do about it
Artificial Intelligence’s ability to augment and support progress and development over the past few decades is inarguable. However, when does it become damaging, contradictory even? In our latest Beyond Data podcast AI’s Climate Jekyll & Hyde – friend and foe, Tessa Jones (our VP of Data Science, Research & Development) and Sophie Chase-Borthwick (our Data Ethics & Governance Lead) discuss exactly this with Joe Baguley, Vice President and Chief Technology Officer, EMEA, VMware.
SOX Compliance Audit Preparation And Checklist
What is FedRAMP?
That’s a good question if you’ve been curious about what it is and if it applies to you. For example, do you have a cloud product that the US Government would gain benefit from using? Are you being asked to seek a security approval or an “ATO” by your customer? We’ll go through the basics of FedRAMP in this article to help you understand where you stand in that process. FedRAMP is a government-wide program.