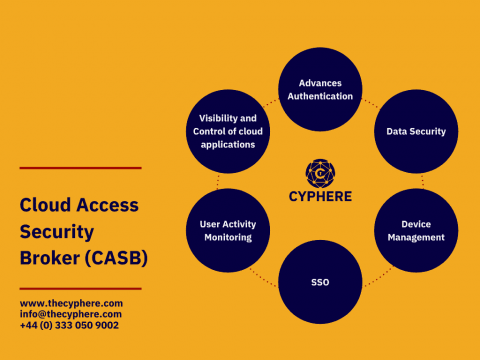
What is a Cloud Access Security Broker (CASB security)?
Cloud access control is a critical part of cloud security strategy. Without granular controls in place, unauthorized users could gain access to your data or even take down your entire cloud infrastructure. Solutions such as Cloud access broker solution (CASB) help you enforce access controls by acting as a layer separating users and cloud service providers.