SAST and SCA: Better together with Snyk
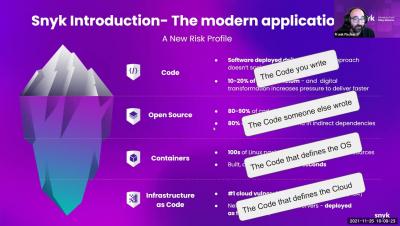
As applications become more complex, so does the task of securing them. While the source code making up applications consists of proprietary code, a great deal of it is also third-party, open source code. Development and security teams looking to release secure code while also maintaining a rapid pace of development, need to therefore combine static application security testing (SAST) and software composition analysis (SCA) as part of a comprehensive software security strategy.