Thick Client Single Sign-On (SSO)
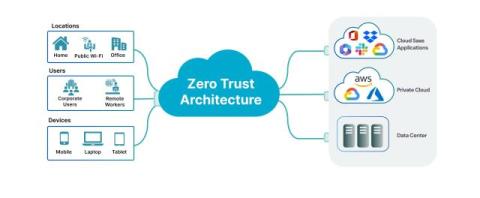
Are you tired of remembering passwords for all your thick client apps, or are you leaving your passwords at vulnerable places and entering them manually every time? Try miniOrange Thick Client Single Sign-on for seamless and secure access. Log in once to miniOrange dashboard and install our desktop software to access all your standalone thick client applications running, boosting your productivity and security.