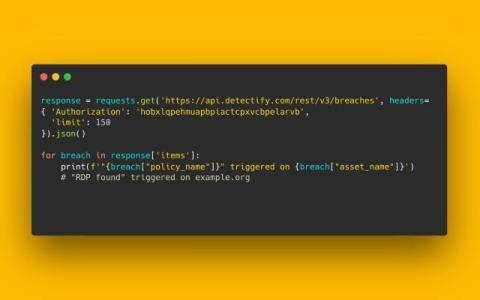
CVE-2024-6387: New OpenSSH RegreSSHion Vulnerability Gives Hackers Root Access on Linux Servers - 700,000+ Linux Boxes Potentially at Risk
Labeled as CVE-2024-6387, the recently discovered vulnerability in OpenSSH has become a serious cause for concern among Linux servers. OpenSSH is a collection of networking tools built on the Secure Shell (SSH) protocol. It is widely utilized to secure remote logins, manage and administer remote servers, and transfer files through SCP and SFTP. Nicknamed as the “RegreSSHion Bug”, Researchers at Qualys initially identified the vulnerability in May 2024.