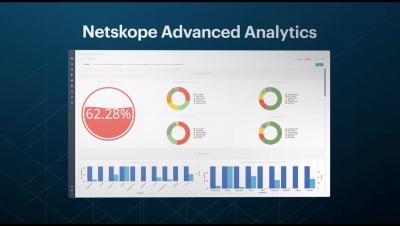
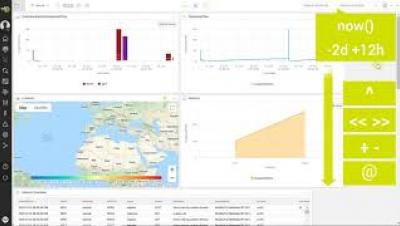
Introducing Netskope Advanced Analytics
Visualize. Investigate. Adapt. Netskope Advanced Analytics is a business intelligence and big data analytics platform providing organizations with 360° views of their cloud risk posture for apps, users, and data.