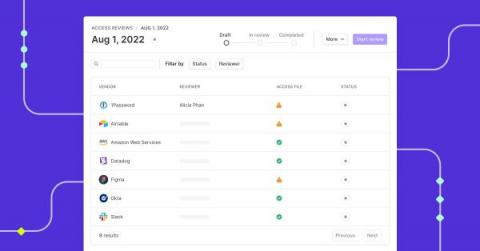
How do you perform quarterly access reviews?
Savvy organizations usually deploy some type of identity and access management (IAM) solution. IAM solutions leverage the principle of least privilege (POLP), role-based access control (RBAC), or other such mechanisms to manage access to data, applications, and IT infrastructure. However, every organization's structure and human resources capacity typically change over time as new employees are brought on board and existing ones quit.