How to secure your cloud services with CSPM
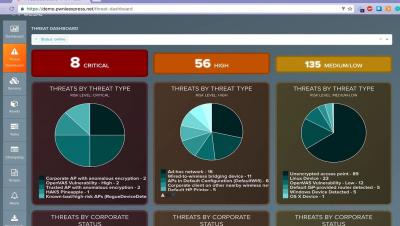
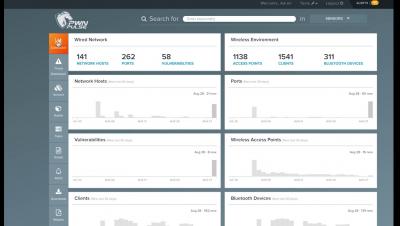
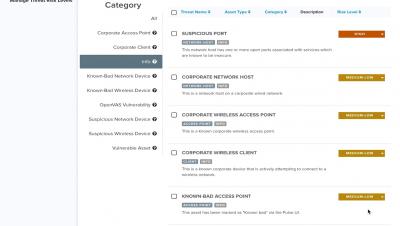
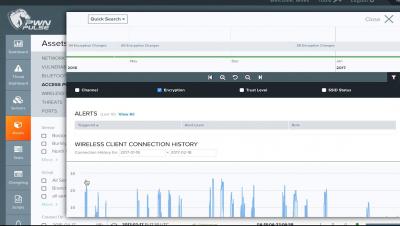
As enterprises fast track cloud adoption plans without security considerations, we’ve seen the dangers of cloud misconfigurations and how it continues to cost millions in lost data and revenue for failure to comply. In this blog we’ll explain how to spot the telltale signs and secure your clouds with adequate Cloud Security Posture Management (CSPM).