Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Synopsys
Build Trust In Your Software | Synopsys
Learn more about Synopsys Software Integrity: https://www.synopsys.com/software-integrity.html
Subscribe: https://www.youtube.com/synopsys
Follow Synopsys on Twitter: https://twitter.com/sw_integrity
Top seven logging and monitoring best practices
Need to build a logging and monitoring solution and unsure where to begin? Get started with our logging and monitoring best practices guide. By: Nivedita Murthy, senior security consultant, and Ashutosh Rana, senior security consultant, at Synopsys.
AppSec Decoded: Why Biden's executive order should be on your radar | Synopsys
How to cybersecurity: Heartbleed deep dive
Over seven years later, the Heartbleed vulnerability still offers important lessons in application security. Heartbleed is a serious vulnerability discovered in the openssl open source software component in April 2014. This article is a deep dive on Heartbleed and its broader implications for application security.
Top 10 Spring Security best practices for Java developers
If you’ve reached this page, you’re probably familiar with Spring and its basic mechanisms already. From its inception in 2002, Spring has become one of the dominant frameworks to build any kind of web application in Java. Web applications usually are the biggest interface between a company and its users—both internal and external. When security is neglected at the developer level, applications can become very desirable targets to hackers.
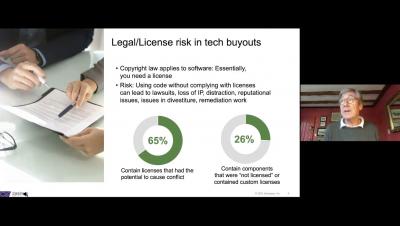
The state of mergers and acquisitions wheeling and dealing
The most recent Transaction Advisors M&A Strategy Forum was held (virtually) in September and offered a wealth of information about deal tactics and terms. Transaction Advisors promotes best practices in all facets of M&A. (Full disclosure: Synopsys is a sponsor of the forum; we find the content very relevant to our clients.)
CyRC Vulnerability Advisory: SQL injection, path traversal leading to arbitrary file deletion and XSS in Nagios XI
CVE-2021-33177, CVE-2021-33178, and CVE-2021-33179 are SQL injection, path traversal, and XSS vulnerabilities in the popular application, service, and network monitoring software Nagios XI.
Building a software Bill of Materials with Black Duck
In an effort to secure the software supply chain, Black Duck SBOM export capabilities now comply with the NIST standards in Executive Order 14028.
BSIMM: Top five software security activities that create a better software security initiative
Looking to build trust in your software? Start with BSIMM12’s top five software security activities. For any organization looking to improve the security of its software, Building Security In Maturity Model (BSIMM) has dozens of options. Many dozens. The 12th iteration of the BSIMM report, released September 28, details 122 software security activities (also known as controls) that were observed in the 128 participating organizations.