Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Zenity
Where is Low-Code Going in 2022? 8 Hot Trends and Predictions (Part 1)
What’s the trick to staying competitive in 2022? The ability to quickly adjust your business models and processes. You need only rewind to 2020 to see why. A worldwide pandemic. The need to create new business models, innovate new business processes, establish new means of interacting with customers… with little warning and small budgets. And all this just to stay afloat. For many of the businesses that succeeded, low-code development solutions were part of their success.
Bye-bye 2021, you have been a blast
Zenity is proud to be the first and only governance and security platform for low-code/no-code applications, and of the unique path we have traveled to get here. Living and breathing technology in every aspect of our lives, we started as a small, enthusiastic team in love with the idea of application development democratization and what it takes to make sure that it is done securely.
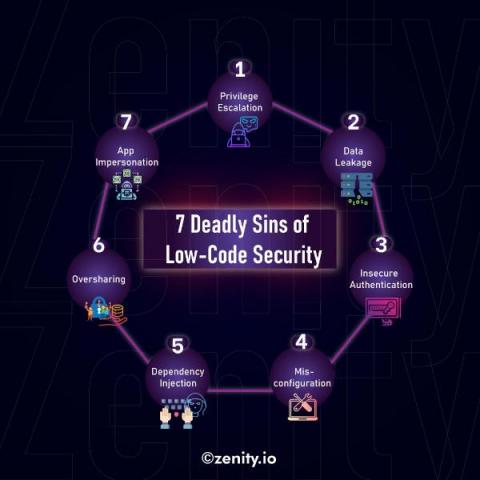
Low-code Security Risks: 7 Sins and How to Overcome Every Single One
Low-code security vulnerabilities can be deadly - but not for you. Learn how to mitigate all the risks involved by downloading our free whitepaper “7 Deadly Sins of Low-Code Security and How to Avoid Them”. If you’ve followed our last two blog posts, you should already be familiar with the reasons why organizations that are undergoing digital transformation are turning to low-code development.
CTO Michael Bargury's Thoughts on Low-Code Security Featured on Dark Reading
We are proud to have thought leaders at the head of Zenity. Michael Bargury, Zenity co-founder and CTO, recently published an in-depth piece on Dark Reading, one of the most widely read cybersecurity news sites and online communities for cybersecurity professionals. The piece was chosen for Dark Reading’s “The Edge,” a featured section that presents deep dives into cybersecurity issues.
Low-code is driving a tectonic shift in IT - can IT and security teams enable the business while also staying secure?
In recent years, we have witnessed a tectonic shift in the way organizations develop and maintain software. As part of this shift, IT operations are quickly getting decentralized.
The Microsoft Power Apps Portal Data Leak Revisited: Are You Safe Now?
In late August 2021, a major data leak exposed where 38 million private records through Microsoft’s Power Apps portals, a powerful low-code tool that enables both professional and citizen developers to create external-facing applications. The misconfiguration was discovered by the research team at UpGuard and is now well-known as one of the most severe low-code security incidents to date.
Citizen Developers Security Awareness
Citizen developers are now producing the types of applications once reserved for professional programmers. By using the low-code/no-code capabilities found in low-code application development platforms (LCAP), business workflow automation or RPA, they can bypass drawn-out development processes and reap the benefits of speed and efficiency. Perhaps even more significant is the resulting efficacy—because who knows better than the citizen developer what the company needs to solve its pain points?
Low-Code for Dummies - An Overview of Low-Code Through Examples
While the mission statement of the Zenity Low-Code Security Blog is to help organizations adopt low-code platforms securely and with confidence, we often find ourselves explaining basic low-code concepts and principles - mostly to those who are not familiar with the day-to-day low-code development process.
Hackers Abuse Low-Code Platforms And Turn Them Against Their Owners
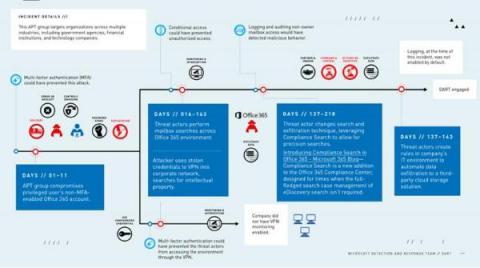
Low-code development platforms open the way for greater independence and efficiency for business users. Unfortunately, they sometimes also open the way for attackers, as a result of poor low-code security practices, especially as low-code application security tries to catch up with traditional application security. Last year, Microsoft’s Detection and Response Team (DART) published the timeline of an attack which leveraged Power Platform, Microsoft's low-code platform.