Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Lookout
3 Things To Know About Securing Remote Work with VPN
It's been two decades since the introduction of virtual private networks (VPNs), and they are still the go-to solution for many organizations that need to connect remote users to company resources. But while VPN technology remained relatively static — grounded on the principle that your resources are primarily located on a corporate network — remote work requirements have changed dramatically.
Are Your Private Apps Secure? 3 Questions To Ask
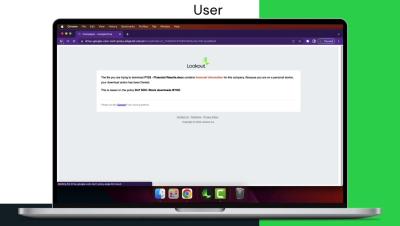
Your data has left the premises. While virtual private networks (VPNs) used to be the go-to solution for extending access to private apps to remote users, they aren't a sufficient solution for securing a hybrid workforce. Because they place so much trust in users and devices, they end up granting overly permissive access to everything inside the perimeter, putting your data at risk.
Top 5 Disadvantages of VPN | Talk Data To Me
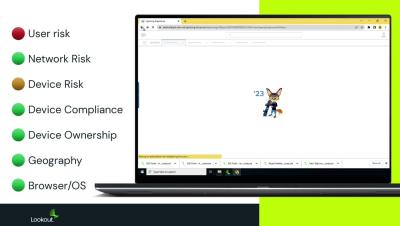
Adaptive Access To Apps Based on User Risk Score and Device Posture with Lookout
Provide Agentless Access to SaaS and Private Apps with Lookout
What is Lookout Secure Private Access? A ZTNA Solution
Navigating the Federal Threat Landscape | Talk Data To Me
Busting 6 Myths About Mobile Device Security
These days, mobile devices are integral to the way we work, and many employees spend their days switching between their phones and their computers. While most organizations have a robust cybersecurity strategy in place to protect their laptops and corporate networks, mobile devices are often left underprotected. And that’s a big problem because mobile devices are frequently faced with risks like phishing attacks and operating system vulnerabilities.
ZTNAs Address Requirements VPNs Cannot. Here's Why.
When organizations were forced to shift to remote work during the pandemic, they needed a quick-fix solution that would enable their remote employees to securely access work resources. For many, this solution came in the form of VPNs. However, VPNs were not designed for the bring your own device (BYOD) and cloud app security use cases. While VPNs can provide remote access, it may come as a surprise that they fall short when it comes to security.