Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
IT Security Risk Assessment Methodology: Qualitative vs Quantitative
Formulating an IT security risk assessment methodology is a key part of building a robust information security risk management program. The two most popular types of risk assessment methodologies used by assessors are: A risk assessment is a process that aims to identify cybersecurity risks, their sources and how to mitigate them to an acceptable level of risk.
Obtaining an API key for the Google Calendar API
Facebook and Twitter warn some users' private data was accessed via third-party app SDK
Facebook and Twitter have announced that personal data related to hundreds of users may have been improperly accessed after users logged into third-party Android apps with their social media accounts. According to a report by CNBC, users of Android apps that made use of a software development kit (SDK) named oneAudience may have unwittingly shared information such as their email addresses, usernames and recent tweets.
5 Digital Threats to Watch Out for on Black Friday
The end of November is a busy time in the United States. On Thanksgiving, friends and family gather together to give thanks for good food and good company. Once they’ve put away the leftovers, many Americans don their coats and head to the malls for Black Friday. The official start to the Christmas shopping season, Black Friday is exciting because many retailers announce limited-time sales that promise huge savings to die-hard consumers.
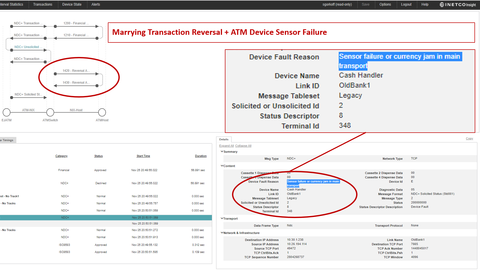
Security Update: Transaction Reversal Fraud - UK Edition
On November 21st, NCR issued a security alert for a new form of Transaction Reversal Fraud (TRF) occurring in the UK, typically between 10 PM and midnight on any given day. Contrary to previously reported TRF attacks in which cash is pried from the dispenser after a payment reversal is initiated due to the jamming of the card reader, this new method does not require any interaction with the card reader or the use of modified cards.
Detectify Connector with AWS Route 53
Last year Detectify announced that we were AWS Technology Partners which meant that getting started with Detectify was made easier. This year we are thrilled to announce the release of a connector between AWS Route 53 to Detectify.
Vendor Risk Assessment Questionnaire Template
A vendor risk management questionnaire (also known as a third-party risk assessment questionnaire or vendor risk assessment questionnaire) is designed to help your organization identify potential weaknesses among your third-party vendors and partners that could result in a data breach, data leak or other type of cyber attack.
Security for Cloud Services: PaaS Deep Dive
Traditional IT organisations have seen significant gains in adopting Platform as a Service (PaaS) solutions. In this blog post, the second in a series looking at the ways to adapt your security operations to reflect the new technologies of cloud solutions, we’re going to look at what you should consider when implementing your security controls for a PaaS environment.
Ransomware: 'Tis the Season for Retailers to be Prepared
‘Tis the season! Winter holidays are upon us, and with it brings the yearly high-volume online shopping season we all know as Black Friday/Cyber Monday (BFCM). With the total US consumer spending estimated at over $717 billion in the 2018 BFCM season, retailers know that the next few weeks are a critical time for their infrastructure. Unfortunately, so do ransomware attackers.