Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Google Chrome Aims to Keep its Edge Over Other Browsers with its Latest Privacy and Security Features
Google Chrome may currently enjoy the numero uno position in the world of browsers, but it is starting to feel the pressure. The competition is heating up with its rivals like Microsoft Edge offering upgraded security features to lock in more users. The coronavirus pandemic has brought extensive changes to the way people operate, which in turn, has created a need for securing remote workforces.
Should Organizations Be Concerned About Nation-State Cyber Attacks?
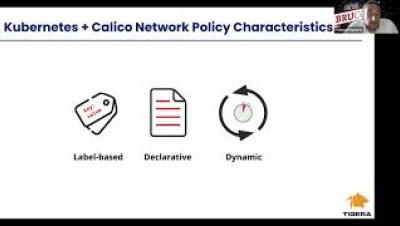
Egress access control for Kubernetes
Code Sight (IDE Plugin) 2020 Update | Synopsys
Learn more about Synopsys Software Integrity: https://www.synopsys.com/software-integrity
Subscribe: https://www.youtube.com/synopsys
Follow Synopsys on Twitter: https://twitter.com/sw_integrity
Code Sight (IDE Plugin) Demo 2020 | Synopsys
Learn more about Synopsys Software Integrity: https://www.synopsys.com/software-integrity
Subscribe: https://www.youtube.com/synopsys
Follow Synopsys on Twitter: https://twitter.com/sw_integrity
Design and Implementation of OEM ICS Cybersecurity Frameworks
Malware Detection: Protecting your reputation and financial bottom line one transaction at a time
While major, multi-million dollar man-in-the-middle attacks have remained under the radar in recent months, spear phishing and social engineering attacks are on the rise as fraudsters continue to take advantage of the uncertainty surrounding COVID-19.
WarXing in Cyber Security
Warcarting, war dialing, wartoothing, wardriving, wartransit… Also known as NetStumbling or WILDing, WarXing is a search of Wi-Fi networks. Keep reading to learn more! In our hyper connected world, an active and stable internet connection is akin to oxygen. Our smartphones, tablets, computers and even smart watches need internet connection to fulfil the entirety of their functions.
Five reasons to consider outsourcing your organisation's cyber security
This issue has been compounded in recent months due to the impact of COVID-19 on IT and security spending. Research by Gartner suggests that worldwide expenditure on information security and risk management technology and services is due to increase by only 2.4% in 2020 – significantly less than the 8.7% growth originally anticipated. To be effective, cyber security requires not only technology but the skilled security experts and threat intelligence to leverage it.