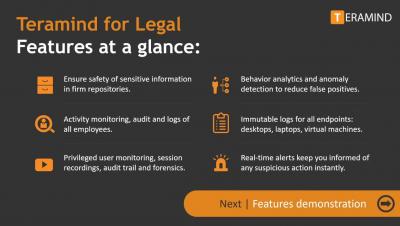
Meet the Hacker: europa: "I always trust my gut when I get the feeling that something is there"
Meet the hacker europa, a white hat hacker on the Detectify Crowdsource platform. He is based in Italy with a great passion for infosec and relatively new to the bug bounty scene, but seasoned in infosec. We asked him about the kind of bugs he likes to find, why he joined Crowdsource and how persistence helped him turn a duplicate finding into a bug with 8 different bypasses.