Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Monitoring
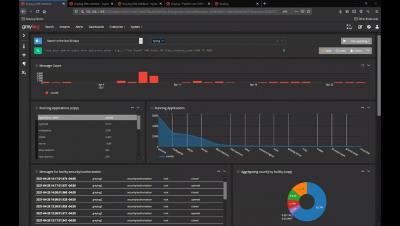
HTTP JSON Web API Input - COVID Dashboard
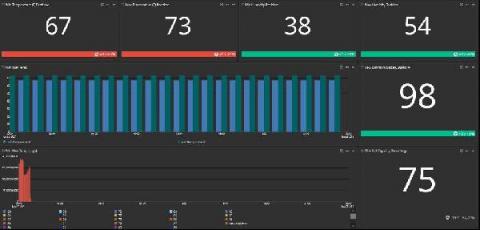
Metric Alerts
New Logs Screen
Bolster OT Security with Graylog
Anyone tracking the evolution of the IT industry is probably familiar with the concept of Industry 4.0. Essentially, it describes the process by which traditional industrial tasks become both digitized and continually managed in an IT-like fashion via modern technologies like cloud computing, digital twins, Internet of Things (IoT) sensorization, and artificial intelligence/machine learning.
Docker Compose on Raspberry Pi4
What's New In 4.1
Endace and Kemp Technologies Partner to Provide Security and Network Teams with Deep Network Visibility
How to detect security threats in your systems' Linux processes
Almost all tasks within a Linux system, whether it’s an application, system daemon, or certain types of user activity, are executed by one or more processes . This means that monitoring processes is key to detecting potentially malicious activity in your systems, such as the creation of unexpected web shells or other utilities.
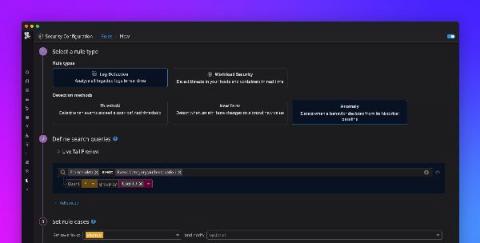
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly