Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Sumo Logic Helps ABinBev Modernize its Security Operations Center
A Quick Guide To Visibility And Smarter Monitoring
Companies of all sizes are learning that when it comes to keeping their digital assets safe; being able to monitor what’s going on within their environments makes all the difference. Unfortunately, those same companies have struggled with basic fundamentals such as maintaining accurate asset inventories and deploying the right technology on those assets to gain visibility into their security posture – two components critical to the effectiveness of traditional visibility programs.
How to prevent crime on the Deep Web and Dark Web
Sir Tim Berners-Lee invented the World Wide Web in 1989, and then it became available to the general public by 1991. The web is an internet service that was designed to help scientists and academics exchange information more effectively. But by the late 1990s, the web helped to make the internet popular and accessible to ordinary people all over the world. Over thirty years after Berners-Lee’s first proposal for the web-- that technology has revolutionized everyone’s lives.
Detectify now checks for File Disclosure in SSL VPNs - Pulse Secure and Fortinet
Pulse Secure and Fortinet have announced advisories detailing a critical vulnerability found that enables an unauthenticated user to conduct file disclosure in SSL VPN. Thanks to Detectify Crowdsource hackers, Detectify checks your website for these vulnerabilities and will alert you if your version of Pulse Secure or Fortinet gateway is affected.
What is a Cyber Attack?
A cyber attack (or cyberattack) is any attempt to expose, alter, disable, destroy, steal or gain unauthorized access to a computer system, infrastructure, network, or any other smart device. In some cases, cyber attacks can be part of a nation-states cyber warfare or cyber terrorism efforts, while other cybercrimes can be employed by individuals, activist groups, societies or organizations. Strong organizational wide cyber security controls are now more important than ever.
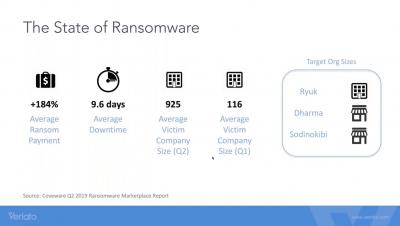
The Rise of Ransomware As A Service (RAAS)
Industrial Cybersecurity in Corporate IT vs. Plant Floors
Survey: 84% of Security Pros Said Their Organizations Struggled to Maintain Security Configurations in the Cloud
Headlines continue to suggest that organizations’ cloud environments make for tantalizing targets for digital attackers. Illustrating this point, the 2019 SANS State of Cloud Security survey found “a significant increase in unauthorized access by outsiders into cloud environments or to cloud assets” between 2017 (12 percent) and 2018 (19 percent). These findings beg the question: how prepared are organizations to defend themselves against cloud-based threats?
Block newly-registered domains to reduce security threats in your organisation
It’s no secret that there are a lot of websites on the internet hosting malicious content whether they be phishing pages, scams or malware itself. Every day we hear of new attacks, there’s a common denominator of either a user having clicked on a link to a fraudulent website or a site having played host to code that pulled a malicious payload down from a third-party server.