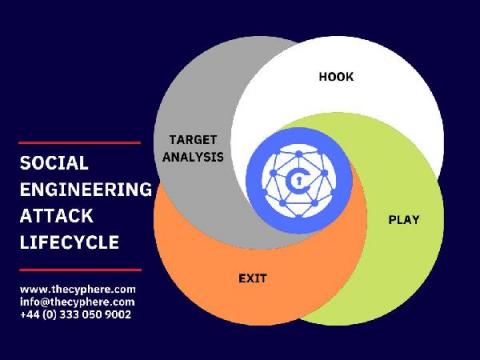
Common Types of IT Security Risks: How to Prevent them?
Many different types of IT security risks can affect a business. It is essential to know about the implications, how cyber risks can be identified and what you need to protect against them. In this connected world, cyber attacks are a common occurrence. As long as the internet exists, there will be information security risks and malicious attacks that come with it. Ranging from minor nuisances to devastating consequences, hackers never seem to stop attacking your data!