Best Practices for Using Tripwire Enterprise in Dynamic Environments - Part 1
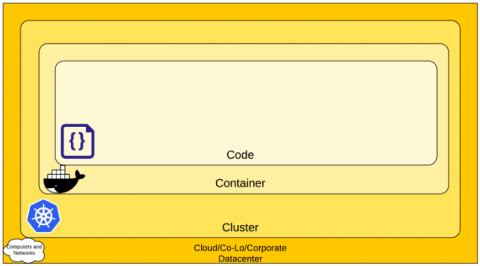
Just a few years ago, most IT environments were made up of deployed servers on which personnel installed applications, oftentimes as many as that one system could handle. They then remained and ran that way for years. In the meantime, the IT team maintained the system and updated the applications as needed. Sometimes there were test versions of those systems, but this wasn’t often. Even then, the OS often didn’t match the production version of the same system.