Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
5 Security Automation Myths Debunked
It has been argued that automation in the workplace tends to be misunderstood. Analysts are keen to point out that, despite myths to the contrary, automation isn't going to put most people out of work, for instance. Nor is AI going to become a real substitute for actual human intelligence. These are compelling arguments for rethinking the way we think about automation in general. But you can take the points further if you analyze the impact of automation on specific domains, such as cybersecurity. Indeed, automation is perhaps nowhere more misunderstood than in the realm of cybersecurity. To prove the point, here are five common myths about automation's impact on security, and why they're wrong.
What are Threat Intelligence Feeds?
Threat intelligence feeds enable organizations to stay informed about indicators of compromise (IoCs) related to various threats that could adversely affect the network. These feeds also help to inform tools like SecurityScorecard’s Security Data by providing a source of information to collect, analyze and share with customers.
What is Cyber Resilience?
Since the covid-19, the cyber incident ratio has drastically increased and shows no signs of settling down. In just one year, cyber-attacks have targeted big enterprises, government agencies of the world’s leading countries, educational institutes, non-government organisations (NGOs), and small to mid-sized businesses. It is estimated that threat actors carry out cyber attacks every 39 seconds, which is relatively faster than before.
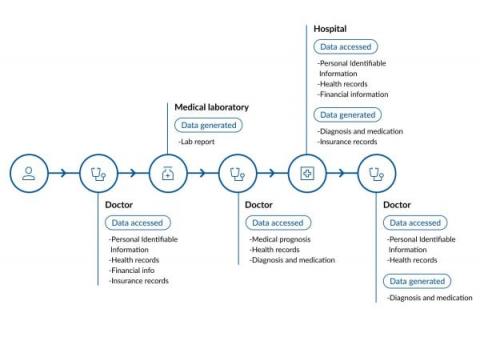
Big Data challenges in tele-healthcare
Covid-19 pushed the boundaries of both healthcare and technology providers, and nudged people to finally embrace telehealth services. In fact, telehealth has proven to be the next frontier for the healthcare industry as it minimizes the need for in-person patient, clinic, or hospital visits which prevents overwhelming our healthcare systems. A McKinsey report shared that the use of telehealth in the US in 2021 surged 38 times compared to pre-pandemic levels.
How to better secure user authentication protocols
In March 2021, cybersecurity researcher Le Xuan Tuyen discovered a security bug in Microsoft Exchange Server. The vulnerability, dubbed ProxyToken, lets attackers bypass the authentication process to access victims’ emails and configure their mailboxes.
Customer Corner: RCBC Bank CTO on Balancing Risk and Innovation
Rizal Commercial Banking Corporation (RCBC) begun as a small development bank in the Philippines and has grown to encompass a wide range of financial services and branches in the U.S., Europe, Australia and New Zealand. Like any financial institution, it must comply with a host of regulations and is a prime target for malicious actors.
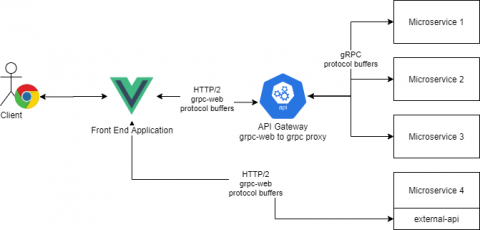
gRPC-web: Using gRPC in Your Front-End Application
At Torq, we use gRPC as our one and only synchronous communication protocol. Microservices communicate with each other using gRPC, our external API is exposed via gRPC and our frontend application (written using VueJS) uses the gRPC protocol to communicate with our backend services. One of the main strengths of gRPC is the community and the language support. Given some proto files, you can generate a server and a client for most programming languages.
Adopting Zero Trust and SASE as Fed and SLED Agencies Go Remote-First
The global pandemic further accelerated a trend toward remote work that was already underway, even in federal, state, and local agencies that previously resisted it. But as agencies continue to offer telework options to employees, they must also rethink their security stack to better mitigate the cybersecurity risks that remote work catalyzes. Traditional, perimeter-based approaches to security will no longer work in a cloud-first environment where data can, and is, accessed from just about anywhere.
Don't Warn Your Co-Workers About That Phishing Test
It is October 2021, and another Cybersecurity Awareness Month is upon us. With so much having occurred over the last year, we should all be experts in personal cybersecurity protection. After all, when our homes became our primary business location, it all became very personal. I once worked at a company that prohibited me from offering personal cybersecurity advice.