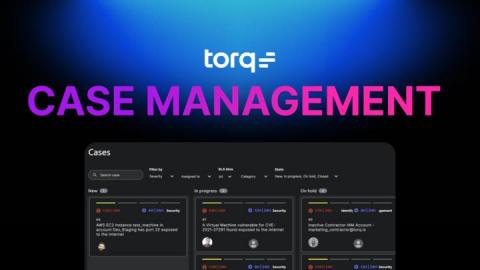
Discover how attackers exploit DNS vulnerabilities in Active Directory
A DNS server is an integral part of an AD environment. Simple yet crucial activities are accomplished using DNS servers, such as authenticating, searching for computers, and identifying domain controllers. But attackers know there are a lot of loopholes in DNS that they can exploit. And, they often already know about these vulnerabilities. In this blog, you will learn how attackers can abuse.