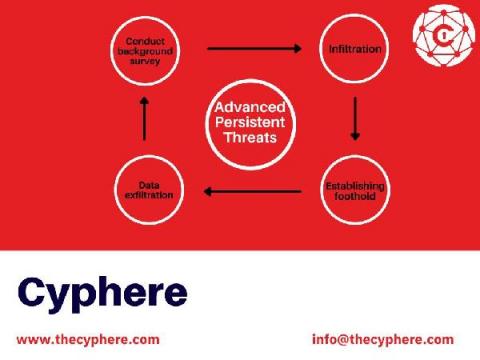
What are Advanced Persistent Threats (APT attacks)
An Advanced Persistent Threat is a sophisticated (rarely) multi-staged attack carried out by skilled and well-organised threat actors such as organised cybercrime syndicates and nation-state actors. The majority of the times, Advanced Persistent Threats (APT) are nothing more than a fancy name with much more media frenzy around the topic of cyber attacks.